
ESET Protect Mail Plus Security For Business
ESET Protect Mail Plus is a scalable and customizable solution that keeps you one step ahead of any threat.
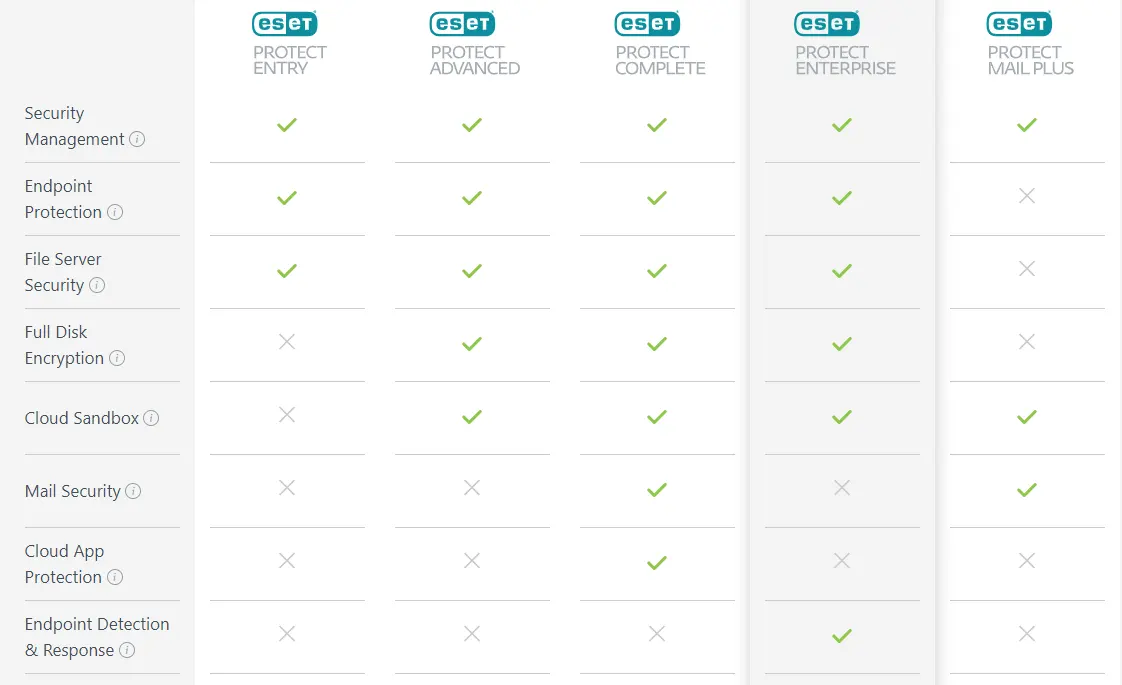
ESET Protect Mail Plus is a comprehensive security solution for all business sizes
ESET PROTECT MAIL PLUS SUMMARY
Cloud‑Based & On-Premise Console
✅ Full Security Management - from Prevention to Response
✅ Automated security management and threat remediation
✅ Flexible, comprehensive reporting
✅ Complete network visibility
✅ Includes
ESET PROTECT
cloud or on-premises
Cloud Sandbox
✅ Ransomware and zero-day threats detection
✅ Powerful cloud sandbox analysis backed by machine learning techniques
✅ Behavior-based Detection
✅ Granular reports with detailed information about samples and their behavior
✅ Includes
ESET Dynamic Threat Defense
Mail Security
✅ Multilayered technology filtering spam and malware
✅ Anti-phishing protection
✅ Protection for the server's file system
✅ Robust quarantive management
✅ Includes
ESET Mail Security
ESET PROTECT COMPLETE COMPONENTS
CLOUD-BASED & ON-PREMISE CONSOLE
Dynamic & custom reporting
ESET PROTECT provides over 170 built-in reports and allows you to create custom reports from over 1000 data points.
Advanced RBAC
Starting with MFA-protected access, the console is equipped with an advanced Role-Based Access Control (RBAC) system.
Completely multitenant
Multiple users and permission groups can be created to allow access to a limited portion of the ESET PROTECT console. This allows full streamlining of responsibilities across large enterprise teams.
Cloud MDM
A ready-to-use solution, integrated with our cloud management console. It’s easy to get started for organizations of any size, as it requires no prerequisites such as certificates or additional components. Cloud MDM covers Android phones, with iOS being on the roadmap.
Cloud sandbox
The support for cloud sandbox greatly improves detection of zero-day threats such as ransomware by quickly analyzing suspicious files in the powerful ESET cloud sandbox.
Granular policy control
Organizations can set up multiple policies for the same computer or group and can nest policies for inherited permissions. In addition, organizations can configure policy settings as user-configurable, so you can lock down any number of settings from the end users.
Always the latest features
Leave the updating of the console up to us. We’ll do it in the background, and you’ll always be on the latest version with the latest components.
Automation framework
Dynamic groups can sort computers based on current device status or defined inclusion criteria.
SIEM & SOC support
ESET PROTECT fully supports SIEM tools and can output all log information in the widely accepted JSON or LEEF format, allowing for integration with Security Operations Centers (SOC).
Full disk encryption (FDE)
Full Disk Encryption is native to ESET PROTECT, managing encryption of data on both Windows and Mac (FileVault) endpoints, improving data security and helping organizations solving the problem of data regulation compliance.
Hardware / software inventory
Not only does ESET PROTECT report on all installed software applications across an organization, it also reports on installed hardware.
Fully automated VDI support
A comprehensive hardware detection algorithm is used to determine the identity of the machine based on its hardware. This allows automated re-imaging and cloning of non-persistent hardware environments. Therefore, ESET’s VDI support requires no manual interaction and is fully automated.
CLOUD SANDBOX
Ransomware and zero-day threats detection
Detect new, never-before-seen types of threats. ESET utilizes three different machine learning models once a file is submitted. After that, it runs the sample through a full sandbox, simulating user behavior to trick anti-evasive techniques. Next, a deep learning neural network is used to compare the behavior seen versus historical behavioral data. Finally, the latest version of ESET’s scanning engine is used to take everything apart and analyze it for anything unusual.
Transparent full visibility
Every analyzed sample status is visible in the ESET PROTECT console, which provides transparency to all data sent to ESET LiveGrid®.
Automatic protection
The endpoint or server product automatically decides whether a sample is good, bad or unknown. If the sample is unknown, it is sent to ESET Dynamic Threat Defense for analysis. Once the analysis is finished, the result is shared, and the endpoint products respond accordingly.
Mail Security protection
Not only does ESET Dynamic Threat Defense work with files, but it also works directly with ESET Mail Security, to ensure that malicious emails are not delivered to your organization.
Granular reports
An admin can create a report of ESET Dynamic Threat Defense data in the ESET PROTECT console. They can either use one of the pre-defined reports or make a custom one.
Mobility
Nowadays, employees often do not work on the premises. The Cloud Sandbox analyzes files no matter where users are.
Proactive protection
If a simple is found suspicious, it is blocked from execution while ESET Dynamic Threat Defense analyzes it. That way, potential threats are prevented from wreaking havoc on the system.
Tailored customization
ESET allows per-computer detailed policy configuration for ESET Dynamic Threat Defense so the admin can control what is sent and what should happen based on the receiving result.
Manual submission
At any time, a user or admin can submit samples via an ESET compatible product for analysis and get the full result. Admins will see who sent what and what the result was directly in the ESET PROTECT console.
MAIL SECURITY
Anti-spam
Now using an enhanced, award-winning engine with improved performance, this essential component filters all spam emails and keeps user mailboxes free of unsolicited or undesired messages.
Anti-malware
Our second layer of protection built into ESET Mail Security provides detection of suspicious or malicious attachments to prevent users from being infected.
Anti-phishing
Prevents users from accessing web pages that are known to be phishing sites. Email messages can contain links that lead to phishing web pages. Such emails are filtered.
Hybrid Office 365 scanning
Supports businesses who utilize Microsoft Exchange in a hybrid setup.
Robust quarantine management
In case messages are quarantined, users receive emails via which they can handle the message management themselves. In addition, administrators can have summary reports sent to them on a regular basis. However, anytime someone is waiting for an email, an administrator can easily decide to delete or release messages from a central quarantine.
Unparalleled speed
Performance and stability are among the essential capabilities for a mail product. Companies need assurances that their email is going to be processed without delay. ESET features a true 64-bit product that allows for clustering to ensure that speed is never a concern for organizations of any size.
Rules
ESET’s comprehensive rule system allows administrators to manually define email filtering conditions and actions to take with the filtered emails.
Web-based quarantine
Emails are automatically provided to users about their spam emails that were quarantined. Then users can log in and manage their own spam rather than this solely being managed by the admin.
Cluster support
ESET solutions support creating clusters, which allows products to communicate with each other and exchange configuration, notifications, greylisting database info and more. In addition, this supports Windows Failover Clusters and Network Load Balancing (NLB) clusters to allow for Enterprise-grade protection.
Flexible and scalable
ESET Mail Security enables component-based installation, providing admin with an opportunity to select only a certain solution component. Also, ESET Mail Security allows exclusion of specific objects or processes from on-access scanning, thus minimizing interference with the process to improve backup speed and process integrity.
ESET PROTECT MAIL PLUS
OTHER ESET PROTECT CLOUD SOLUTIONS












Reviews
There are no reviews yet.